Charting the Roadmap to Prevent, Detect, Manage and Respond to Cyber Security Threats

Security Operation Centre as a Service
Idnor’s team of experts with over 12+ years of cybersecurity and IAM experience analyze your current organization infrastructure, data and application layer, help you build your strategy, test your capabilities, and advance your team. The increasing cybersecurity talent shortage is making it difficult and expensive to attract and retain skilled personnel.
Idnor’s SOC-as-a-Service offerings allow an organization to outsource their security responsibilities to a third-party provider. Instead of manning a full-service SOC in-house, the SOC-as-a-Service provider takes responsibility for the round-the-clock network monitoring and defence required to protect against modern cyber threats.
Benefits of hiring Idnor for SOC as a Service:
Benefits of hiring Idnor for SOC as a Service:
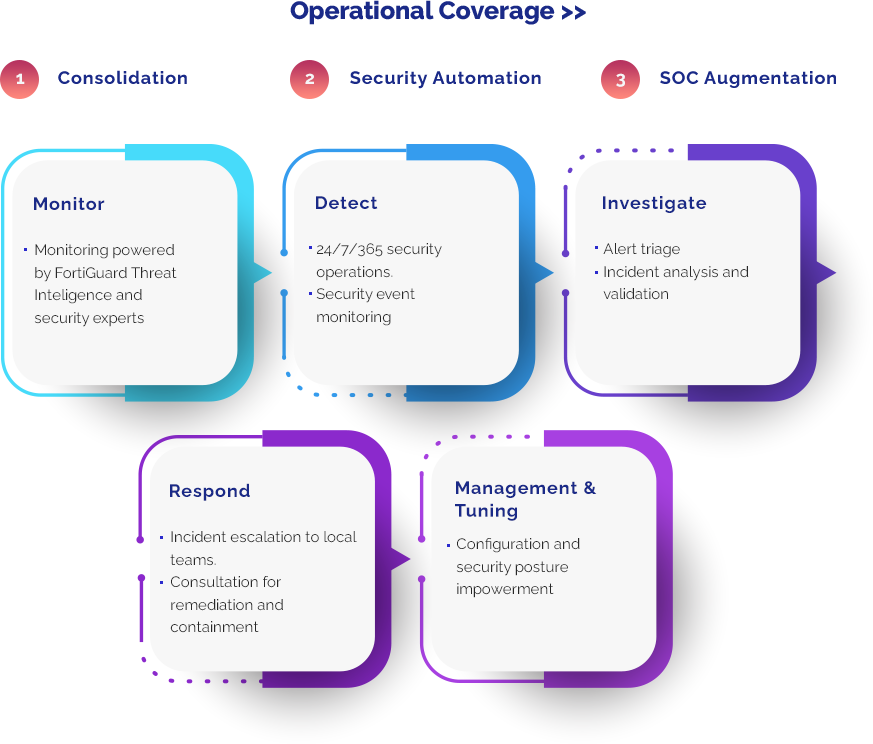
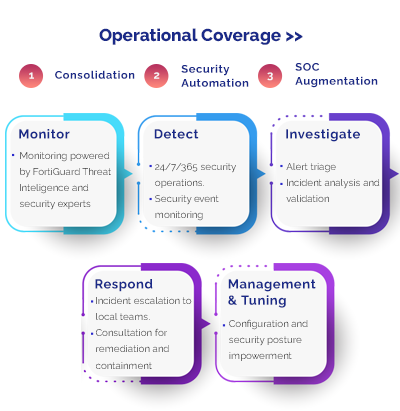
Cybersecurity Maturity Assessment
Idnor measures your organization’s cybersecurity maturity to help you protect your future. Ageing infrastructure, unsupported software, decentralized asset management, and mergers and acquisitions have created technical environments that are increasingly difficult to manage. As the threats from cyber criminals grow in scale and variety — how can organizations employ effective cyber capabilities to rapidly adapt to the ever-changing security landscape and confidently drive growth and strategies through digitally enabled products, services and business transformation?
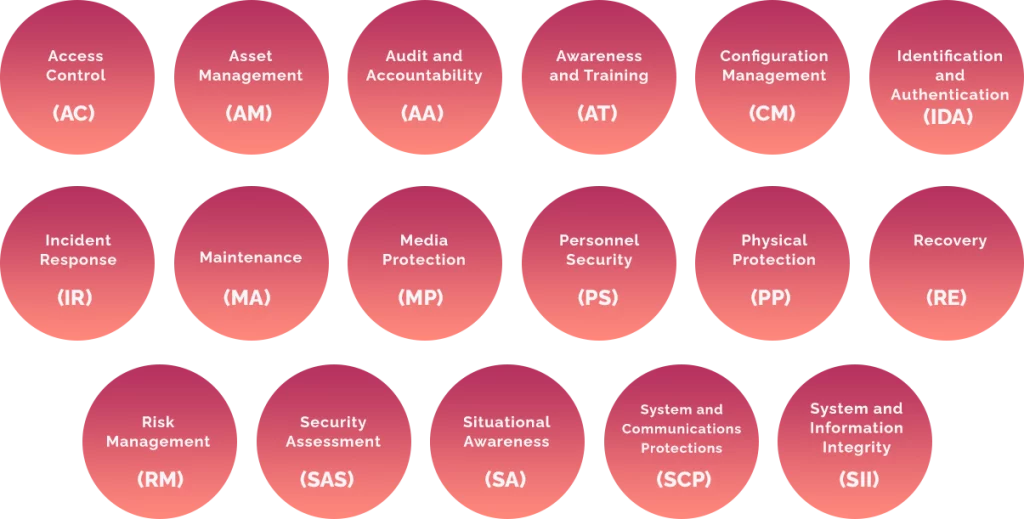
“The Cybersecurity Maturity Model Certification (CMMC) is a security framework by the US Department of Defense (DoD) that aims to eliminate vulnerabilities in the supply chain and improve security practices.” Idnor helps use this model to change your current insights into decisions for your organization. We conduct a comprehensive risk assessment (CMA) of your organization’s readiness to prevent, detect, contain and respond to threats to information data, applications and systems. We help you do a 360-degree company analysis of people, processes and technology.
It provides insights to understand vulnerabilities, identify and prioritize areas of remediation, and demonstrate corporate and operational compliance. By outlining the cyber capabilities that require the focus of the board and translating them into an operational, business-enabling function, the CMA will help you to support and achieve business objectives, manage risk, build trust and measure performance — turning information risk into business advantage.

DevSecOps - Deliver Software Faster With Secure DevSecOps
In recent times, the DevOps adoption has led to a significant transformation in enterprise computing deriving several value-added benefits such as increased agility, speed and reduced costs, in addition to features such as serverless computing, dynamic provisioning and pay-as-you-go cost models. But it has been wanting in some cases, secure delivery of code which is ‘DevSecOps’.
DevSecOps (development, security, and operations) is a development practice that weaves security initiatives at every stage of the software development lifecycle to deliver robust and secure applications. Whether you need help evaluating, testing, or building a deployment pipeline, or an assessment of your overall DevSecOps strategy, our team at Idnor has the knowledge and proven experience to support your organization without compromising on quality or speed of delivery.
Talk to Our DevSecOps Expert Today
As organizations evolve their IT culture to DevOps by shifting their focus to rapid service delivery through the adoption of agile and lean practices, we enable teams to inject comprehensive application security testing at the right time directly into the software, at the right depth, with the right tools and processes, and with the right experience.
Work With Us:
or fill out the form on this page.
