Define, manage, and audit with Privileged Account Management and Idnor


Privileged access management or privileged account management is a system that ensures that privileged
accounts remain free from any vulnerability. This system typically looks into the entire privileged account lifecycle,
starting from granting and revoking permissions of these accounts to having a fail-proof password change cycle.
Most PAMs use the principle of least privilege, wherein they start by giving zero permission across all accounts and
incrementally add them as necessary.
The goal of privileged account management is to discover and monitor privileged accounts, bring down
unnecessary entry points into the system (because of which the ‘attack surface of the organization decreases), and
enable better password hygiene. It does so by establishing a unique identity for every employee in the company.


However, as the adage goes, “Trust but verify.” Privileged account management (PAM) lets you control and
monitor your privileged accounts. You need to be able to revoke privileges at any time. Think of privileged
accounts like giving a good friend a key to your home.
If you learn later that they have been stealing from you, you want to be able to get your key back and change the
locks instantly. PAM lets you do this for your organization’s data and network.

Privileged account management in the enterprise
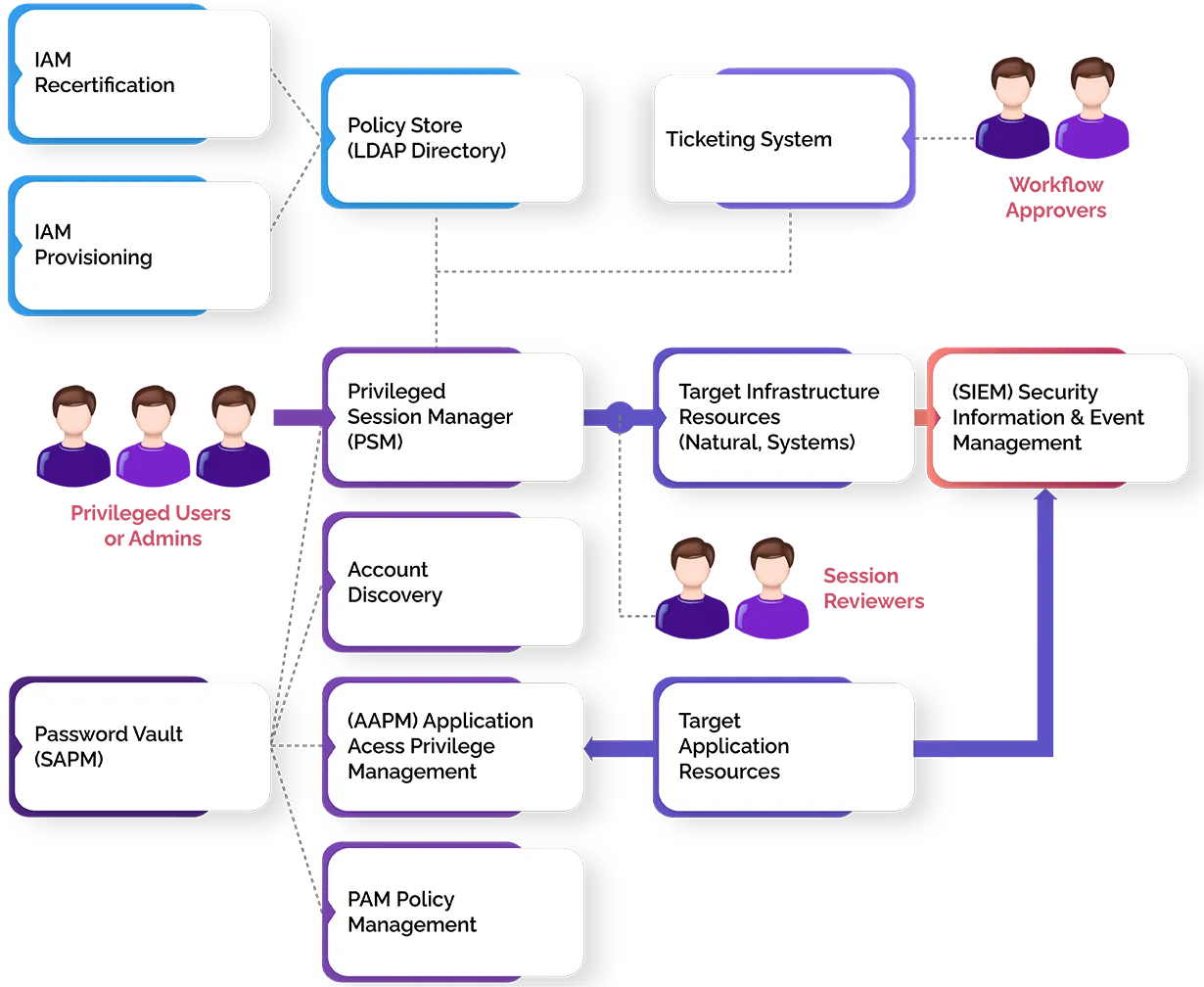
Types of privileged user accounts
Superuser accounts
These are top-of-the-pyramid accounts with unparalleled access to systems across the
network. These are used to create and maintain other user accounts and grant and revoke permissions as and
when required.
Administrative accounts
Administrative accounts can control all devices and users within a local setup (local
administrative accounts) or a specific domain (domain administrative accounts
Administrative accounts
Administrative accounts can control all devices and users within a local setup (local
administrative accounts) or a specific domain (domain administrative accounts
Emergency accounts
These are fallback accounts that administrators can turn to if their original accounts are
compromised or face any issue.
Benefits of using PAM

Helps discover and report privileged accounts

Improves workflow and productivity

Addresses compliance regulations

Manages and secures passwords

Manages access points

Monitors privileged user sessions for anomalies

Protect the Keys to Your Valuable Assets with Idnor
Work With Us:
Put identity security at the core of securing your business
Contact us today and we will put you in touch with one of our IAM experts to discuss how you can take full advantage of our flexible security solutions.
Give us a call: 508-906-5090/+91 7799075678
or fill out the form on this page.
or fill out the form on this page.
