Protect your IT ecosystem. Establish trust. Ensure secured user access.

Access Management
Access management is the authentication of an identity that is asking for access to a particular resource, and access decisions or called authorization are simply the yes or no decision to grant that access.
This can be a tiered process, with access services that determine whether a user is authorized for any access on the network at all, and lower tiers of access that authenticate where the identity in question should be granted access to specific servers, drives, folders, files, data, systems and applications. Authorization for any given application or resource will be determined by the identity’s attributes, such as which group(s) it belongs to, it’s level in the organization or a specific role that was previously assigned.
As with authentication, the granting of authorization can occur in multiple tiers within the organization, for example, both as a centralized service and again locally for a given application or resource, although authenticating at the resource or service level is frowned upon as central authentication provides more consistent control.
This can be a tiered process, with access services that determine whether a user is authorized for any access on the network at all, and lower tiers of access that authenticate where the identity in question should be granted access to specific servers, drives, folders, files, data, systems and applications. Authorization for any given application or resource will be determined by the identity’s attributes, such as which group(s) it belongs to, it’s level in the organization or a specific role that was previously assigned.
As with authentication, the granting of authorization can occur in multiple tiers within the organization, for example, both as a centralized service and again locally for a given application or resource, although authenticating at the resource or service level is frowned upon as central authentication provides more consistent control.
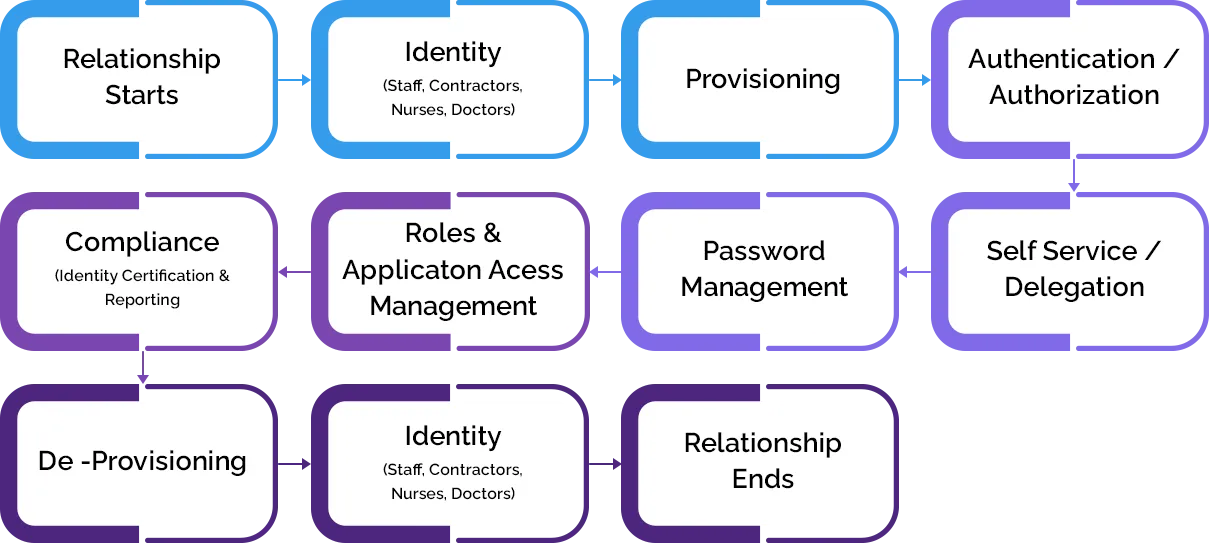
What are the business benefits of Access management?

The ability to successfully protect assets – including digital assets – can have a direct bottom-line impact on the
value of the organization. IAM accelerates the time to value for anyone who needs access to enterprise resources
to perform their job, often speeding the time between onboarding a new employee until when they have access to
system resources from days to minutes.
Besides providing an enhanced business value as a result of improved security, there are other tangible business
benefits. Automation of IAM tasks frees up IT for bottom-line focused projects, and self-service identity
management tools improve the overall productivity of employees, contractors, and other users who access
corporate resources.


Idnor helps you secure your organization’s critical resource access:
We implement an overall IAM framework can provide growth opportunities, by improving the scalability of those
services critical to onboarding new users. Reducing IT manpower translates to a better ROI for the IT organization
as a whole.
Contact us today for a centralized access control
Work With Us:
Put identity security at the core of securing your business
Contact us today and we will put you in touch with one of our IAM experts to discuss how you can take full advantage of our flexible security solutions.
Give us a call: 508-906-5090/+91 7799075678
or fill out the form on this page.
or fill out the form on this page.
